Hosting your own password management instance
BItwarden to the rescue!
I have always had trouble remembering my passwords. And with time as the services grew, it became even harder. Now, there were two options for me to overcome this problem -
Keep a log or text file on my pc - This seemed like a very good option. But this method is not entirely proof as
- The file may get corrupted accidently.
- Any kind of exploit or attack on my pc can make this file vulnerable.
- I may accidentally delete my file.
- Keeping it in plain text can allow anyone who has access to my machine, to access my credentials.
Store it on 3rd party applications - Well this seems like a good plan. But I honestly don't trust any 3rd party server/application to keep my credentials. Imagine if they have a CVE or a bug or any vulnerability. That would be disastrous, isn't it. And honestly, no matter how secure the systems claim to be, security is a myth (my favourite hacker line!)
Now there was only one way to have the best of both worlds. A self-hosted password management service that provides the following features -
- No involvement of 3rd party services
- All-round web plugins and apps to sync my credentials from all my devices.
- I own the data and have the flexibility to port it at my will.
And, I found all my requirements fulfilled by Bitwarden
Bitwarden is an Open Source application that can manage all your credentials, card details, sensitive documents, etc. It has a self-hosted option and 3rd party hosting service(never trust anyone else with your creds!).
Without further ado, let's start in the guide of how to have your own Bitwarden instance up and running. Pre-requisites for this guide -
- Create an account on Google Cloud Platform (They give $300 as a joining bonus, so that should help you to host your instance literally for free!)
- Have a domain name (you can choose a subdomain of your own choice)
Steps to host your instance
Setup SSH
- On the GCP console, create a new VM. This should be under the category of compute engine. Follow this video for the steps.
- If you are a windows user follow this
- Choose f1 micro machine with 30 GB storage, as the hosted instance won't require much computing power (thus saving you money)
- Setup SSH for your newly created machine. You can follow this guide for the same.
- SSH into the machine and run the following commands to update your machine -
sudo apt-get update sudo apt-get upgrade
Install Docker
- Install Docker in your machine via the following commands -
sudo apt-get install apt-transport-https ca-certificates curl gnupg-agent software-properties-common sudo curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add - sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable" sudo apt-get update sudo apt-get install docker-ce docker-ce-cli containerd.io sudo systemctl enable --now docker - Confirm that you can run docker commands. The following command should return without errors and show zero running containers.
sudo docker psInstall Bitwarden_rs
- Now we will install Bitwarden_rs image. Pull the bitwarden_rs image.
sudo docker pull bitwardenrs/server:latest - Select the desired file system path to store application data. In this guide, the path /srv/bitwarden is used. Create the directory if necessary, and enforce strict permissions for the root user only.
sudo mkdir /srv/bitwarden sudo chmod go-rwx /srv/bitwarden Create the Docker container for bitwarden_rs.
sudo docker run -d --name bitwarden -v /srv/bitwarden:/data -e WEBSOCKET_ENABLED=true -p 127.0.0.1:8080:80 -p 127.0.0.1:3012:3012 --restart on-failure bitwardenrs/server:latestThis command uses the following flags to establish a persistent container to serve the bitwarden_rs application:
- -d daemonizes the container to run in the background.
- Using --name bitwarden gives the container a human-readable name to avoid the need to reference the running container by a temporary identifier.
- By passing the host path /srv/bitwarden to the volume (-v) flag, data is persisted outside of the container whenever it is stopped.
- The environment variable WEBSOCKET_ENABLED enables the extra websocket server for bitwarden_rs.
- Each -p flag forwards the respective host ports to the container (port 8080 for the main bitwarden_rs web service and port 3012 for websocket traffic). Normal HTTP and HTTPS ports are served with Caddy.
- --restart=on-failure ensures that the container remains up in the event of container failure or host restart.
As part of these steps, note that the container listens for traffic on the local loopback interface (127.0.0.1) and not a publicly reachable IP address. This is to ensure that any traffic originating from outside the host must connect to the Caddy server, which enforces encrypted TLS connections.
Installing Caddy
External clients communicate with Caddy, which automatically manages reverse proxying WebSocket traffic. Caddy also provisions and renews TLS certificates via Let’s Encrypt automatically.
- Pull the Caddy alpine image.
sudo docker pull caddy/caddy:alpine Create the following Caddyfile. Be sure to replace example.com with the name of the domain that you set up in the Before You Begin section of this guide, and confirm that the domain points to the IP address of the Linode. This domain serves as the web interface for bitwarden_rs hosted and secured by Caddy’s automatic TLS.
File: /etc/Caddyfileexample.com { encode gzip # The negotiation endpoint is also proxied to Rocket reverse_proxy /notifications/hub/negotiate 0.0.0.0:8080 # Notifications redirected to the websockets server reverse_proxy /notifications/hub 0.0.0.0:3012 # Send all other traffic to the regular bitwarden_rs endpoint reverse_proxy 0.0.0.0:8080 }
Note - The site name you choose in this file must match the desired URL that bitwarden_rs is served under. When navigating to the web interface later in this guide, ensure that you type the same hostname chosen in this configuration file (in this example, example.com).
- Prepare a directory for Caddy in /etc to store state information such as Let’s Encrypt certificates.
sudo mkdir /etc/caddy sudo chmod go-rwx /etc/caddy - Start another Docker container to run a persistent caddy daemon.
sudo docker run -d --name caddy -v /etc/Caddyfile:/etc/caddy/Caddyfile -v /etc/caddy:/root/.local/share/caddy --net host --restart on-failure caddy/caddy:alpine
Initial Setup
- Navigate to the chosen domain in a local web browser (in this tutorial, example.com). Verify that the browser renders the Bitwarden web vault login page, and that the page is served over TLS/SSL.
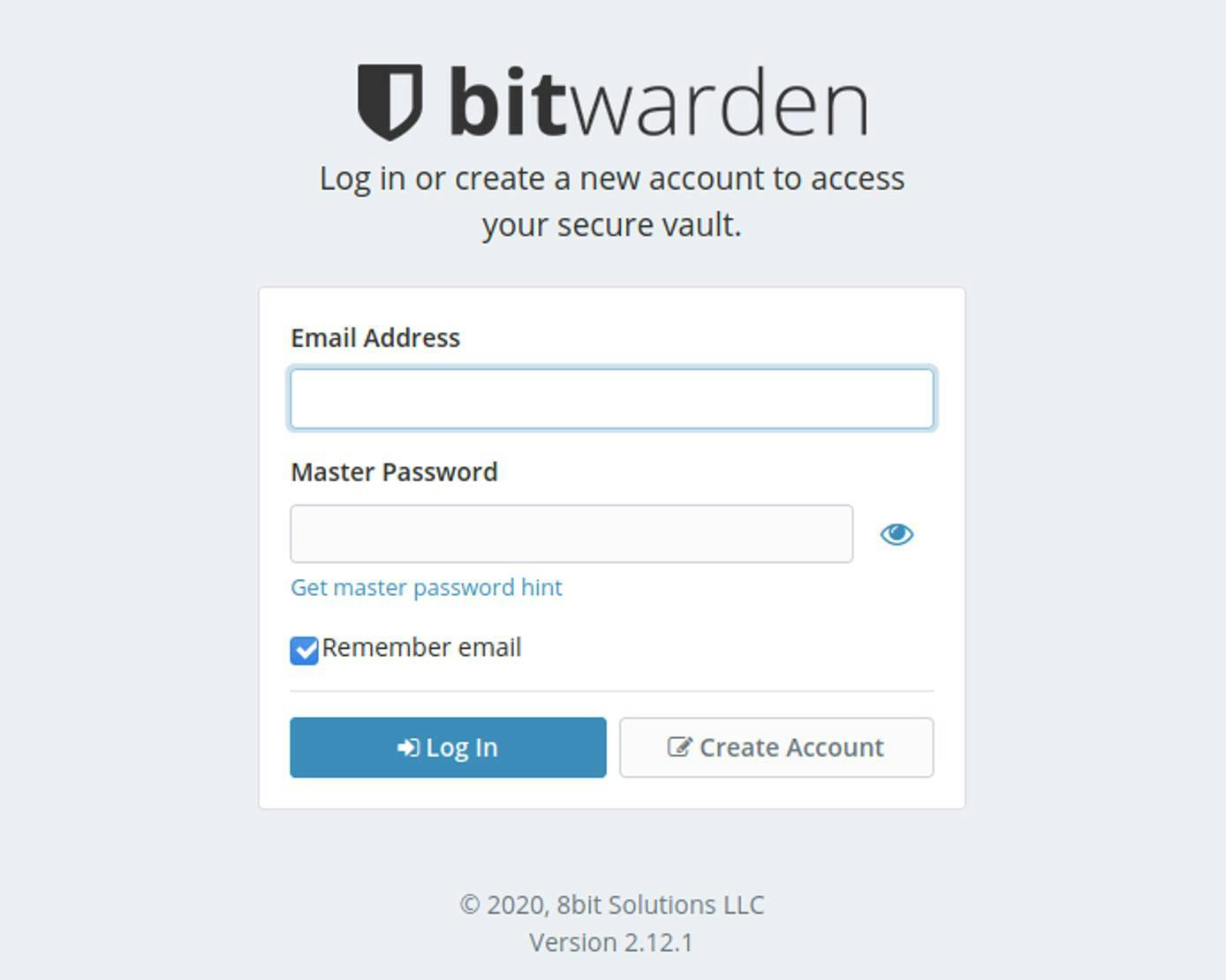
If you see the login page, congratulations! bitwarden_rs is running and operational. The first step in using the password manager is to create an account. Do so by clicking on the Create Account button on the login page.
- A new page appears with several fields.

Fill each field with the appropriate information, choosing a strong and secure master password.
- After registering, the system redirects you to the login screen. Log in with the credentials. The web vault view appears.

And that's it. Now you can download the Bitwarden web browser plugin and various mobile applications and have it use your vault from settings (setting it to your domain!)
Hope that this article was useful for you. If you face any issues, please let me know down in the comments. Your feedback is highly appreciated. Have a good day!

